Archive for the ‘GNU/LINUX’ Category
a Pythonic Linux Sharepoint Services?
summery
WSS is great but it likes people with deep pockets (MS IIS License). Go open source instead XD
I guess one of the benefits of working for a company that is very close to Microsoft is getting to know all their “solutions” first hand. One of these solutions is Windows Sharepoint Service. basically, it’s an application suite that allows people who are working on a project to work better with one another by organizing the way information is managed and accessed while providing methods to organize team work and increase team efficiency.
How did they do it? will it’s simple really, they just jam a blogging platform, a forum, subversion control, and a wiki into on system and provide exceptional integration with MS Office.. thats all.
Why should i give a *? will for starters, this can be the perfect solution for developing software. as you may have noticed, almost all major projects have a Sharepoint like system, one way or another. sourceforge, gnome live, and so on.
OK, now two problems remain: It’s proprietary and it costs money. I’ve searched the net and found an open source sharepoint clone released by Alfresco (google it) but it’s more oriented towards replacing microsoft’s sharepoint technology than providing a platform for POSIX servers. it even integrates with Office!
One solution is to write my one tailored sharepoint system. that, or wait until someone else writes one. I’m probably going to write one myself (most likly using python since it’s very convenient for web applications) if i get the chance.
i’ll probably design it for technical projects rather then general purpose, it might include:
• a Mailing list/forum
• a basic file management system
you might wonder why i intend to write the previous tools all over again appose to using will established tool already available. the answer is simple:
no need for separate passwords for each system and so on
• Each tool instance would be specific to the project it serves
No more overcrowded forums/bug trackers. when you access the tool it will only represent the it’s parent project.
In conclusion, I hope I don’t need to write the thing. but if no other sutable choices exist, i’ll probably have to write it anyways. as usual, any feedback is appreciated 🙂
SIGTERMer
PS: I might also integrate OO.o if it provides the necessary functionality, and if i have enough time to read on the subject.
Documenting your projects with DOCBOOK
click on three links bellow then click around:
bash
secure programming
Docbook
if you did click around, you would have probably noticed something; all the documents are presented in a consistent way even though they where written by deferent people, living in deferent places.
if you were adventurous, and went up a few directories you might have noticed that each document had a pdf version, and that each pdf of the three was organized in the same way as the other.
can it be that each writer thinks in the exact same way? i think not.. at least i hope not.
the tool behind producing these online/offline documents is ether Docbook or LaTex. this article discusses Docbook, an schema (XML or SGML) developed to facilitate documenting software or hardware. However, it is not limited to these two fields. in fact, it can be used to document anything.
Docbook focuses on content structure rather then appearance. this – in my opinion – is what makes Docbook so great. instead of using open office and constantly indenting, changing fonts, spacing paragraphs, and so on, i can focus on what is more important: what i’m actually writing!
the following docbook code:
<book>
<bookinfo>
<title>My software is the COOLEST</title>
<authorgroup>
<author>
<firstname>Sulaiman</firstname>
<othername>A.</othername>
<surname>Mustafa</surname>
</author>
</authorgroup>
</bookinfo>
<chapter id="Introduction">
<title>Introduction: Installing and Starting</title>
<para>
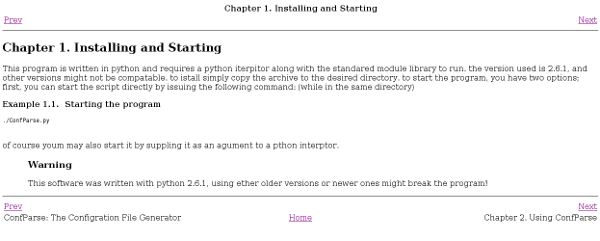
This program is written in python and requires a python iterpitor along
with the standared module library to run. the version used is 2.6.1, and
other versions might not be compatable. to istall simply copy the archive to the desired directory. to start the program, you have two
options; first, you can start the script directly by issuing the following command:
(while in the same directory)
<example>
<title> Starting the program </title>
<programlisting>
./ConfParse.py
</programlisting>
</example>
of course youm may also start it by suppling it as an agument to a pthon interptor.
<warning><para>This software was written with python 2.6.1, using ether older versions or newer ones might <emphasis>break</emphasis> the program!</para></warning>
</para>
</chapter>
</book>
should give:
note that docbook can save in many deferent styles and formats. for more information, you may want to look at this.
SIGTERMer
wget: more versatile then a trusty swiss-army knife
A tool that makes life that much easer…
This is by far the most useful command-line tool when it comes to dealing with the web. wget is a small simple-to-use tool that allows you to get content from other sites. this includes html, tar balls, and anything else the server is willing to provide.
if you’re wandering what good it is when there are numerus browsers that do this, read on.
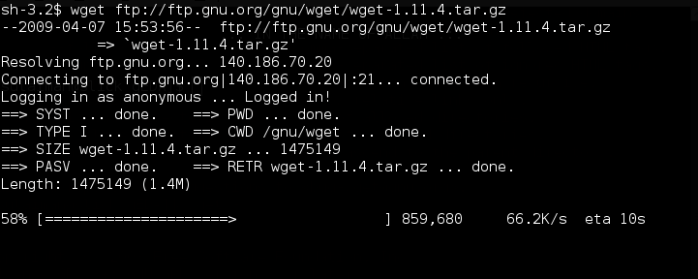
wget (unlike browsers) is a non-interactive tool, meaning it doesn’t need you once it has been given a job. such as downloading an entire directory, say this one. rather than clicking each item on that list, you can simply use wget by issuing this command:
wget -r ftp://ftp.geda.seul.org/pub/geda/release/v1.4
wget can also help by making those pesky online-only documents available off-line. take this for example (i know this is available in downloadable form but this method is applicable on other sites as well)
wget is a well-behaved tool, it will not download from any site that specifies rules prohibiting it. these rules are stored in the root directory of the server (robots.txt). however, most rules are meant to be broken. you can ignore rules by adding the following to the command:
-e robots=off --wait 1
The “wait” has nothing to do with ignoring rules, it simply makes it easer on the server by waiting 1 second between every fetch. please add this when downloading from good sites, and conveniently forget it when downloading from microsoft :p
Also, when recursing, wget will only go down 5 levels. if the site you want to download has a directory structure that goes deeper then this, add
- l
Finally, some sites analyze traffic and can determine if an automated application such as wget is downloading, and can block it. there is an solution to this but i won’t go into it since i never really used it.
enjoy the web with wget 🙂
SIGTERMer
Please don’t read this. move along…
If you’re reading this, that means i’ve failed to stop you from wasting a couple of minutes of your life.. *sigh* don’t blame me.
this is an intractive tutorial gone bad. after wasting hours on it, i decided to upload it (i didn’t want my had work to go to wast). if you you want to download this then click this.
i tried to warn you, but do you listen?
SIGTERMer
Haxorizor: +|-|3 }{/-\><0|2!2()|2 P|20_|3<+ 0\/\/|\|5
The Haxorizor project was started to produce a highly customizable bi-platform dynamic l33t character encoder; it takes in normal alphabetical character and spits out it’s l33t equivalent. it was also started out of boredom. Currently, Haxorizor can be used in live (interactive) mode and for processing entire text files. it should be noted that live mode is available only when the source is compiled for linux and is not available on windows. On the other hand, a full-featured GUI has been made available for Windows users as a separate program that uses Haxorizor to encode characters. it is also included in the package.
Although it’s still in alpha, it can be downloaded here. extract the tar.gz archive and read the installation instruction is the INSTALL file. note that the source is compatible with windows but you’ll need to compile it directly using gcc. linux users can compile and install it using the build.sh script. Any feedback IS appreciated! you can comment here directly or email me at sigtermer.at.gmail.com.
just a note… the title was generated by haxorizor in live mode 🙂
SIGTERMer & Anxious Nut
Working on a Vigilante8-like game.. Any Suggestions
Working on a Vigilante 8-like game.. Any Suggestions?

vigilante8
I intend to write a game that has a mixture of Vigilante8, AirCombat, and an extra dash of sonic. if anybody has any ideas or requests this is the time to speak.
I don’t know how far i’m going to go this time, but there is a good chance i might actually pull it off! although collision detection is still a fogy area for me.
anyways, any suggestions are appreciated.
thanks,
SIGTERMer
Running Windows 3.1 in Linux

Requirements:
1. DOSBox, ways to download it:
a. Open the terminal and type sudo apt-get install dosbox
b. Open Synaptic and download it (assuming you’re using ubuntu).
c. Go to its website and download it.
2. Windows 3.1, finding this was a problem, but I found a website that lets you download it for free, but you’ll have to make an account. Here’s the link: http://vetusware.com/download/Windows%203.1/?id=3391
Steps:
1. Move the -downloaded- Windows 3.1 file/folder to a directory of your choice (Do not change its place after placing it, cause some steps depend on its path), extract it if it was zipped.
2. Open the directory that contains Windows 3.1’s files, you’ll find several folders named “Disk1”, “Disk2”, “Disk3”, …, “Disk7”.
3. Make a new folder named “CombinedFiles”.
4. Return to the directory that contains the disks. Now, move all the files in every disk folder to “CombinedFiles” folder.
5. Open “CombinedFiles” the folder that contains all the disks files, search for a file named “SETUP.EXE”, and open it with DOSBox. Once you’ve pressed it, DOSBox should start running, and then the installation begins.
6. Install it, it wont take time, and every time it asks you to put another disk press “Enter”. The installation should finish without any problems.
7. You’ll be asked whether if you’d to restart your computer or switch to MS-DOS, at that point switch to MS-DOS and quit DOSBox. So type in “exit” and press “Enter”. If that didn’t work, press “Ctrl + F9”. FYI If you didn’t exit DOSBox, Windows will not work in a good way and -probably- you wont be able to use your mouse.
8. Now go to “/home/YourName/” and make a new text file and name it “dosbox.conf”, copy and paste the following (don’t forget to change the path):
========================================================
[autoexec]========================================================
# Lines in this section will be run at startup. Type the following in on a new line:
#mounting
mount C: /home/...path.../CombinedFiles/
C:
9. Now you have two ways to run Windows 3.1:
a. Open DOSBox, type “cd WINDOWS“, and then type “win” and hit the “enter”.
b. Open any *.EXE from “CombinedFiles” with DOSBox, type “cd WINDOWS“, and then type “win” and hit the “enter“.
Notes:
1. To kill DOSBox press “LeftCtrl + F9”
2. To get out your mouse from DOSBox prss “LeftCtrl + F10”
3. It boots in 3 seconds! (if not less)
…enjoy!
Anxious Nut
How to block Ads (ubuntu)
Well, I just knew how to block ads (in Linux, BSD, and SolarisUnixes), so I’m going to share this with you in this short 4 steps tutorial! But before I start, for those who might ask “why would I want to block ads?” “Why should I?” for two things: to have your page loaded quickly and to not be annoyed ever again (… not really, I’ll tell the reason later on)!
Step1. Open nautilus as root.
step2. Change the directory to “/etc/” and open the text file “hosts”.
What you are going to do is that you’re going to insert URLs of ads in the text file and going to redirect that URL to localhost IP(127.0.0.1); so that when the ad wants to load it’ll search in your IP(localhost), but it is not on your PC so it’ll go like “Not Found” which also means blocking ads(you could block unwanted sites too). The good thing is that you don’t have to enter every single ad URL; cause there are some sites which helped us with this; they provided a very long list containing all those URLs(ads)! just like http://www.mvps.org. anyhow let’s continue…
Step3. Copy the list from this page and paste it in “hosts” text file.
Step4. Save the document.
Congratulations, That’s it, you’ve just blocked all the URLs that are in that list. … About what I said before a while ” to not be annoyed ever again (… not really)” the reason is that there might be some new ad sites which are not included so they will appear in your browser, but you can always add the URL to the text file 😉 … and to be honest since I’ve done that till now I haven’t seen a single ad, so enjoy and don’t worry.
Anxious Nut
An easy and rapid GUI design with xmessage RETRO-STYLE (On Linux, BSD, and anything else running X)
Probably at one point in your life, you will wake up wanting to create a GUI fast! whether it’s a front-end for some software you are writing, or just for the heck of it (i said probably). this simple how-to will teach you how to do just that.
The objective of this article is to design a GUI as fast and as effortlessly as possible. if you want more flashy GUI similar to what you usually get when you start a program, I’d recommend glade.
because we want the least effort we will be using bash (yes a terminal) to deploy and manage our GUI. The key player is xmessage (see “man 1 xmessage” for more detail). this is a simple yet incredibly useful program that displays a simple GUI dialog on the screen. its simplest form is:
xmessage "SIG is cool"
try that in your terminal and hit enter. if you did, you will see the following window:

see, even X thinks i’m cool :p
there are other futures that make xmessage more user friendly, and more usable. for instance, add the -default okay switch to activate the okay button when you hit enter. also, you can load an entire text file in the text area by using -file.
now, how about adding a few extra buttons? you can add more buttons by using the -buttons switch. two buttons are added: “yes”, and “no”. “yes” is the default. the command:
xmessage "SIG is cool" -buttons "yes:10, no:11" -default yes
gives:
run it.
at this point you might be wondering how this can help make a robust GUI for your application. this is where bash really comes in. open a text editor and write the following:
#! /bin/bash
xmessage -center "SIG is cool" -buttons "yes:10, no:11" -default yes
answer=$?
if [ $answer -eq 10 ]; then
xmessage -center "You rock man" -default okay
else
xmessage -center ";_; ... i'm not crying ..." -default okay
fi
this is a simple bash script that behaves in the following manner:
"SIG is cool" | +-> yes: "You rock man" | +-> no: ";_; ... i'm not crying ..."
first save your script as “sig.sh”. then add excution permissions:
cd /your/scripts/directory chmod +x sig.sh
once this has been done, simple start the script by issuing: (while still in the same directory)
./sig.sh
or you can double click, and choose run. any way you do it you should get the following:
SIGTERMer
SSH/openSSH Guide
Basically, you can copy, redistribute, and modify as long as the resulting work remains licenses under the same license. This a rough summery of the license and can not be legally used. If any conflicts are found between this description and the official license. The official license (the URL above) is considered correct.
I and the Adnan Alliance Organization can not be held responsible for any damages linked directly or indirectly to this document. USE THIS DOCUMENT AT YOUR OWN RISK. The author and the organization provide ABSOLUTELY NO WARRANTY, TO THE EXTENT PERMITTED BY APPLICABLE LAW.
Have you ever wanted to access your box over a secured network connection? Do have a normal DSL/Modem connection (Your IP changes each time you reconnect or when ever your ISP feels like it) but want to access it from anywhere without checking what IP address? Do you want to access your PC but you workplace has a firewall that doesn’t allow anything except browsing? Well, your in luck, because this guide shows you how to do just that!
This guide assumes that you have Ubuntu up and running. If you have Debian, you may be able to follow this guide. But if you have other distributions such as SUSE or Fedora, you will need to improvise.
Dedication
I dedicate this project to each and every Muslim in Gaza, may God be with you… They WILL pay sooner or later, but they will pay and that’s a fact! Death Tole: Over 1400 innocent people dead in a period not more than a month. Who is the real terrorist here!
Distros Used
I am using Ubuntu for this guide because most beginner tend to use it. for other distoros, you might need to take a few additional steps to get ssh working in the way you want it such as opening ports/excepting connections and so on. personally i use Archlinux, for other arch users, i recommend this.
Setting up SSH
The software that is used to remotely access your computer is called OpenSSH (open secure shell). but throughout this guide, it will be referred to simply as SSH. To access your PC remotely, you need two programs: A client, which is the software that is used to connect to the server. Ubuntu has a ssh client installed by default. And a server, which runs on the computer you connect to (herein referred to as sshd or ssh daemon). You will need to install this if you want access your PC remotely via ssh.
To install the server software (sshd) on Ubuntu:
sudo apt-get install openssh-server
Type in your password and apt-get will start to download the software and will install it automatically once it has finished.
To test the ssh server, type this at the terminal:
ssh localhost
You should get a login prompt indicating that sshd is up and running correctly. If that succeeds, you can go on and try to login from another computer on the same network (nothing that goes through a router/firewall). To login to the server from a deferent computer, type the following:
ssh ?.?.?.? -l username
where ?.?.?.? is the IP address of the computer you are trying to login to. And username is the name of the user you want to use to login with.
Congratulations, you can now control your server from anywhere, as long as you’re connected to the same network the PC is in, or the server is directly connected to the internet (no router, proxy server, or any other network device to hide behind).
Configuring your Router to accept and redirect connections
Unless you plan to use ssh only in your local network, you will need to configure your router to accept connections made to the port the ssh server (sshd) listens to. This port is usually 22. but as you will see later, this port can be changed to any other port to improve security and availability. Since there are countless router manufacturers, it would be imposable to cover each and everyone. And as a result, configuring your router will be left to you. The keywords you will need to search for is port forwarding. Linksys misleadingly calls it “Applications & Gaming”. Just connect to your router by typing its address in your browser. This might be 192.168.1.1 or 192.168.0.1. but it needn’t be one of the two. Just mess around until you find it (assuming that your router supports port forwarding). WARNING: CHANGING ROUTER SETTINGS MIGHT PREVENT YOU FROM ACCESSING THE INTERNET, OR MIGHT PREVENT YOU FROM ACCESSING YOUR ROUTER. PRECEDE WITH CAUSION!
Finding a good Dynamic DNS service
To access your PC from a remote location, you will need to know its address or at least your routers address. This wouldn’t be a problem if you had a static IP. but seeing that most ISPs don’t assign static IPs, you will need to take special measures to insure that you can access your server where you are even if your IP changes. The easiest way to do that is to use a free dynamic domain name service (DNS). There are countless servers available. I have experience with only one service, but that doesn’t mean it’s the best and any DNS service will do. And if you have a domain name (such as example.com) you can also use it but you will need to find a way to update it.
I currently use FreeDNS and have been using it for about 3 months. It provides a good reliable service and has never failed (at least not yet). The downside is that it doesn’t provide official software to automate the process of checking your IP and updating the DNS if required.
Another service that comes highly recommended is http://www.no-ip.com. This service looks good enough but have never tried it. I would recommend this for beginners. I am considering using it myself if and when FreeDNS fails.
To login using a domain name, simply subtitute the domain name with the IP address. The following should clear things out:
ssh DomainName -l username
where DomainName points to the server you want to connect to.
Modifying SSH to get past any Firewall that allows browsing
SSH uses port 22, this wouldn’t be a problem if you were trying to connect from a private network. But most companies and other institutions have restrictive firewalls that reject connections unless these connections are used to preview web pages. In other words, it only allows HTTP (80) and HTTPS 2(443) are allowed. To get around this problem, set the ssh server to listen to ether port one of the two ports. You should be able to fool the firewall into allowing an ssl connection. I recommend using port 443 since SSH uses the same protocol as SSL (HTTPS).
To do this you will need to modify the sshd configuration file. Also, you will need to type in a few more characters each time you want to connect to the server. To set the ssh server to listen to port 443 (or 80), open the sshd config file located at “/etc/ssh/sshd_config”. Search for the line with the following line:
Port 22
Add # before the line, and add a new line after it so that the result would look something similar to this:
#Port 22 Port 443
Of course, you can replace 443 with the number of the port you want to use. After changing this, the command you use to login is as follows:
ssh DomainNameOrIP -l username -p Port
Again, make sure to change Port to match what you chose previously. Use 443 if you’ve decided to set it with 443.
Note: if you are running a web server, port 80 is out of the question. Also, if your web server is set to except SSL connections, port 443 is off the table as well.
X Forwarding Through SSH
SSH has a nice feater called X Forwarding. This allows you to run GUI applications on a remote computer and interact with them just as if they were running on your own pct. Although with Ubuntu, you might have some problems with it at first. But once everything has been set up properly, you’ll be glad it’s there.
To enable X forwarding, simply add the two options XC (case sensitive) as shown bellow:
ssh DomainNameOrIP -l username -p Port -XC
Note that C was added to for better network performance. You might run into problems when trying to use X forwarding, namely the authentication file issue. After searching the web, I have found that the best way to solve it is to delete the file and then reconnect. Ether that or you need to login under root. To test it out, type xclock. A small analog clock should appear.
Securing SSH
ssh was written to allow people to remotely access computers. Naturally, you don’t want the bad guys to gain access to your computer. Although, ssh comes with some security settings by default, it can still be cracked. To improve security there are several things you can do, this guide will list some of them.
Changing the default port:
The first thing that crackers will probably do is preform a port scan and determine what services your server provides. Note that most of these attacks will be automated (as in scripts). Leaving the the default port unchanged will make it very easy for anyone to find out if your server offers ssh or not. To prevent this unnecessary headache, simply change the port sshd listens to (remember, sshd runs on the server side). You may use a technique called port knocking, but I have no experience with it since I never really needed to use it. To change the port sshd listens to: open “/etc/ssh/sshd_config” and search for the line
Port 22
Change the port to whatever you like as long as the port your switching to isn’t in use. I suggest using port 80 if you aren’t using the computer as web page server, or use 443 if the computer isn’t set up to accept SSL connections.
Limiting “MaxAuthTries”:
This option specifies how many chances you get to enter your password before the connection is dropped. This might be useful to slowdown brute force attacks, but if you detect successive login failures. I would strongly recommend using an alternate authentication method such as keys.
Don’t “PermitRootLogin”:
change this to no to prevent anyone who wants to login to your pc under root.
Using keys:
keys can be used to login without typing a letter. With this type of authentication, you can disable interactive login dialogs and therefore destroying any hopes of brute-forcing into your ssh server. I have to admit though, I have yet to use this method. This is primarily because I haven’t seen a single attack so far. But I will probably switch to this type of authentication soon.
Monitoring your server
From time to time, you will need to check on the authentication log to make sure no one is trying to break into your server. To do that, type the following at the server’s terminal:
less /var/log/auth.log | grep ssh | less
This line should display each and every authentication process that has been initiated by sshd. If you see a large number of login failures form unknown address, your server might be under attack. Try changing ports or using ether port knocking or – better yet – keys.
Moving files between server and client
personally I use scp to securely copy my files over the net. scp works in the same way cp does but does so over a secure connection between two separate computers. The syntax of the command is a s follows:
scp -P pornumber source destination
Where: pornumber is the number of the port sshd is listining to (default is 22) source replace this with the path of the file you want to copy. Add ?.?.?.?: in front of the path if the file is on the server side (where ?.?.?.? is the IP Address of the server). And don’t forget the :. destination replace this with the destination of the file(s) you want to copy. It can also have an IP address if you want to copy files to the server.
This guide was intended to glue all the information you might find useful and practical in one place. However, It is not by far the most complete. If you find that one of the sections is not clear enough or just want to learn more, search the net. Or if you want more information on the commands used in this guide, type man followed by the name of the command at the terminal.
Other Resource:
https://help.ubuntu.com/community/SSHHowto
http://www.vanemery.com/Linux/XoverSSH/X-over-SSH2.html
SIGTERMer



